
Tom Lysemose Hansen is on a mission to protect mobile applications from bad actors. Mr. Hansen is CTO of Promon, inventor of the cybersecurity product Promon SHIELDTM. “Mobile Enterprise Security is an increasingly important topic, Mr. Hansen said in a recent interview. “Mobile technology has become mainstream, and security technologies are rapidly catching up. Enterprises now need to define their mobile security strategies for the next five years,” he emphasized.
Promon’s goal is to reduce the risk of data leakage by protecting the apps on mobile devices like smartphones and tablets. Promon SHIELDTM both monitors the operating system and protects software applications on desktop machines, mobiles and IoT devices. The company believes, though, the mid to long-term trend in security for organizations is toward safeguarding against vulnerabilities in the mobile space.
Mr. Hansen sees enterprises continuing to focus on securely enabling the mobile devices their workforces use. Indeed, organizations are looking for more-sophisticated and less-invasive solutions to address a long list of security requirements. “Technologies such as; Application Shielding and Mobile Threat Detection, will be central to this effort,” he said. “They will continue to enjoy adoption.”
Mobile threats can no longer be ignored.

Gartner has found that 53% of organizations surveyed already had mobile applications in their enterprises, while 40% were planning to deploy them in the future.
Mobile applications pose additional levels of risk since much of the business intelligence, and sometimes intellectual property, resides in the application that is downloaded on the employee mobile device. Further, the enterprises cannot be assured that mobile handset providers will roll out software patches frequently enough to address operating systems vulnerabilities.
Another concern arises out of a growing trend of hackers to create fake app versions. Hackers can obtain a public copy of a mobile app, reverse engineer it, place malicious code into the app, and redeploy it to the market. Unsuspecting victims then download and use the app, leaving their credentials and personal information exposed to the hackers, including sensitive corporate data such as financials, credit card accounts, patient records, intellectual property, and customer information.
Mr. Hansen explains, “A decade ago, mobile malware was considered a new and unlikely threat. Today, mobile apps are coming under increasing attack – and no enterprise is immune. Malicious actors continue to pump out new and more deceptive malware, and more than 1.5 million new strains of mobile malware have been detected in the first quarter of the year alone”.
Mr. Hansen also believes that taking a proactive role in shoring up your mobile enterprise security before an attack strikes, by implementing Application Shielding software and best practices to mobile app development, you can enjoy the treats of mobile security without succumbing to the tricks of digital threats.
How to get ahead of the mobile threats?
As enterprises push ahead with mobile-first strategies – and employee smartphones and tablets increasingly become business tools – the importance of mobile threat detection is growing.
The idea behind Mobile Threat Detection software is for the software to sit in the background and monitor the application and the operating system to identify anomalous behaviour. By monitoring the operating system your apps run within, you can determine what is normal and what is abnormal behaviour, and what might lead to a malicious attack. For example, if you have the X amount of mobile devices on iOS 11.1 and most of them have very similar types of firmware, but one of them diverges significantly from what is normal, chances are there is a modified library; that modification is abnormal – and it might be done for malicious purposes.
A recent survey also showed that 75% of the surveyed enterprises had an average of 35 jailbroken or rooted devices, a state that leaves devices completely vulnerable to attacks, since the process strips away all built-in security provided by iOS and Android. With application monitoring and detection capabilities in place, your enterprise is in a better position to determine and to set a risk level score for each device the enterprise application runs on.
The financial value and frequency of malicious attacks on mobile devices exceeded that for PCs in 2017 and mobile devices are essentially the new ‘backdoor’ for cyber-criminals. To proactively combat advanced and persistent mobile threats, Promon believes enterprises should implement in-depth protection and detection that monitors and controls the execution of the application, including the interactions with operating system components, to protect from attacks and data exfiltration. Mr. Hansen explains “Promon SHIELDTM solution does exactly this and it also provides essential security such as; Obfuscation, Anti-tampering and Integrity Checking, as well as White-box Cryptography and many other security features”.
Promon SHIELDTM actively defends applications and more
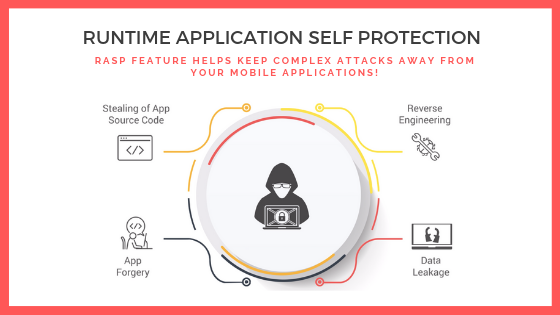
Runtime Application Self-Protection (RASP) is a security technology that is built or linked into an application or application runtime environment. When the RASP software sees that malware is changing the permissions attached to an application, RASP will modify the activity of the application to ensure the attack is not satisfactory.

Whitebox cryptography dissolves keys into the programming code and obscures algorithms, even at runtime. The technique keeps keys safe even when an attacker has complete access to the device on which the cryptographic functions are executing.
Privilege Escalation detection alerts app custodians whether malware has compromised a device’s operating system at the root level. This form of systems subversion is called Jailbreaking or Rooting. Additionally, Integrity Checks can detect whether malware has altered an application. Integrity checks use validations like checksums to ensure apps are secure. They also audit the inventory of libraries and calls included in the software.
Device Binding securely links an authorized user to his device(s). It is crucial for the prevention of cloning or repurposing of cryptographic keys. Anti-debugging / Emulation detection can identify ongoing attacks to a device. It also protects against the use of debug tools that reverse-engineer applications.
Disclaimer: This article has been published SecureMAG Volume 10, 2018





