SECURETMS RA
A Centralised Solution
SecureTMS RA
Top Notch Technology
SecureTMS-RA consolidated both PKI device and with digital certificate lifecycle management into one single centralized system. The system is designed to facilitate better PKI system localization when most of the system customization can be done without touching on the CA Core module. In addition, it extended the external RA implementation via is innovative Distributed RA model.
SecureTMS RA
SecureTMS RA
SecureTMS RA
Plug & Play Support
A complete in-house developed system with built-in plug & play support to full range of SecureMetric’s PKI devices. Total hardware and software solution from a single vendor, minimize integration problems and support hassle.
Open Standard Architecture
Provides configurable connectors to enable flexible connectivity to most external services and systems via a set of developer friendly APIs.
Ease on Bulk Processing
Default support for Bar Code scanner together with secure PKI device batch file upload which will ensure easy processing on bulk PKI devices enrolment and provisioning.
Innovative User Self-Service Facilities
Designed with innovative user-friendly self-service facility aimed at minimizing unnecessary administrator intervention and manual end user support work. Option to provide enhanced PKI user experience implementation via customized PKI workflow automation.
Ready for Customization
Offer customization to meet different client’s operation workflow, security policies, standard operating procedures and digital signature act regulations.
Flexible to Support CA
Built-in CA Management and Configuration modules by default to support SecureCA and/or EJBCA Enterprise but optional to support other CA systems upon request.
Strong Security
Applying latest security methodology in development together by taking advantage on PKI architecture, SecureTMS RA offers strong hardware token based 2FA solution that can fulfill the crucial 4 Trust Requirements (Confidentiality, Authenticity, Integrity, and Non-Repudiation).
Complete Lifecycle Management
Provide complete and reliable way to administer and control PKI devices and digital certificates lifecycle.
High Availability
Built-in with a high-availability configuration by synchronizing the database with a backup Server, either on-site or off-site and ready for Hot Recovery if require.
Powerful Web-based Administration
User friendly with feature rich graphical user interface for User administration via a 2FA HTTPS browser session. Administrators can logon to the Server using a browser to manage the server, without needed to install any specific client application.

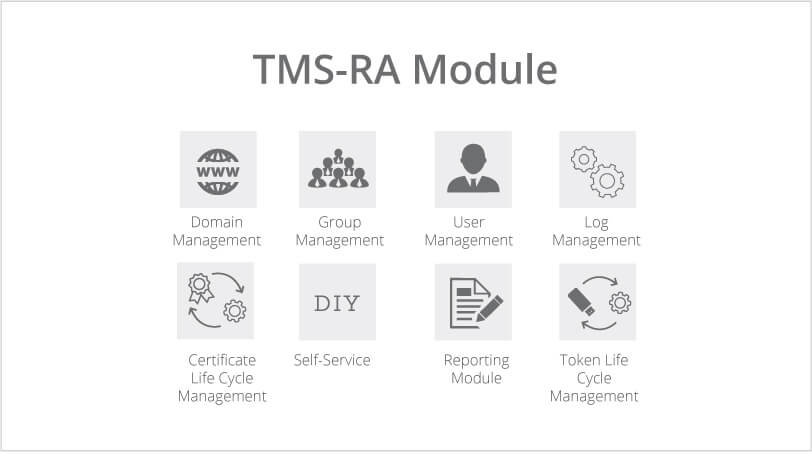
Key Features:
-Non-Smart Chip Based
Commonly based on a typical low cost EEPROM where the main protection algorithms rely more on the firmware that are bundle together rather than on the hardware. This type of hardware architecture can easily be duplicated by most Dongle Duplication Experts
-Self Definable Security Algorithms
Up to 128 self definable security algorithms that will be executed on-board when called by protected software which will then be authenticated using the popular Challenge Response Authentication to maximize the security level of the protection.
-Smart Chip Based
Advanced EAL4+ and ITSEC certified microprocessor smart chips enable the algorithm’s execution and on board seed code generation. Microprocessor smart chips also prevent hardware cloning and duplication attacks.
-Multi Levels Access Right Management
Supports multi level access right management to facilitate different access rights for the development team.
-HID Driverless
As HID driverless, SecureDongle requires no external device driver installation, thus minimizing the common technical issue arise from device driver. No driver is required. As long as a USB thumb drive is compatible with
-User-define security password
Supports on-board seed code and random number generation which developer can apply into their protection to strengthen the security and to make the protection more complicated to crack.
-Secure Communication
SecureDongle is built also with advanced encryption/decryption on communication between firmware and hardware to prevent debugging and emulator attacks.

SecureDongle Brochure
Smarter way to protect your sfotware!
1
%
of software installed on PCs around the world in 2015 were not properly licensed (a decrease from 43% in BSA’s previous global study published in 2014)
1
%
worldwide rate of unlicensed use in banking, insurance and securities industries (despite the fact that much tighter control of the digital environment is expected)
1
billion
The commercial value of unlicensed software worldwide plunged (BSA’s 2014 report cited commercial value of $62.7 billion)
Case Studies
National Cyber Security Agency (NACSA) & Securemetric Berhad
NACSA partners with Securemetric to enhance Malaysia's cybersecurity through FIDO2's passwordless authentication for critical information infrastructures.
Lazada Group’s Transition from EJBCA Community
Securemetric assisted Lazada Group's Transition from EJBCA Community to PKI-in-a-Box
Philippine Clearing House implemented PKI-In-A-Box to secure their clearing system
A significant stride was achieved when the Philippine Clearing House Corporation (PCHC) selected Securemetric to furnish and execute PKI-In-A-Box as a pivotal component of their nationwide digital security enhancement within their payment clearing system.
Universiti Utara Malaysia Entrusted Securemetric’s Microsoft Expertise
Since 2018, Securemetric's Microsoft Enterprise Solutions team, in collaboration with Sri Vision specialists, has been entrusted with the management of Universiti Utara Malaysia's IT infrastructure
Turnkey customized EJBCA Enterprise for Vietnam Government Information Security Commission
In the year 2015, Securemetric achieved a significant feat by securing a contract for a comprehensive turnkey PKI implementation for the Vietnamese Government, executed under the aegis of the Vietnam Government Information Security Commission (VGISC).…
Badan Siber Dan Sandi Negara upgraded to EJBCA Enterprise
Charged by the Indonesian government with the pivotal role of establishing and operating the Indonesia Government Certificate Authority, BSSN is entrusted with the issuance of digital identities and pivotal trust services to governmental entities nationwide.

SecureToken Brochure
SecureToken is an advanced secure microprocessor smart chip based USB token that integrates with powerful cryptographic technology designed for strong 2-Factor Authentication






