HARDWARE SECURITY MODULE
Data & Information Protection
Hardware Security Module
Top Notch Technology
Cryptographic services are essential component in IT security implementation as to protect sensitive information, trust and integrity are derived from the security underlying signing and encryption keys. HSM is the only viable option that can protect those keys while able to perform mission critical cryptography operations within its highly secured and tempered proof environment. HSM is one of the critical elements in most of the PKI and other security solution implementation.
SecureMetric is the certified technical partner for both Ultra Electronic AEP from United Kingdom and Utimaco from Germany. We distribute full range of their HSM products while offering value added cryptography module customization and project implementation services.
SecureMetric is the certified technical partner for both Ultra Electronic AEP from United Kingdom and Utimaco from Germany. We distribute full range of their HSM products while offering value added cryptography module customization and project implementation services.
Utimaco SecurityServer Se Gen2
Utimaco SecurityServer CSE
Utimaco CryptoServer Software Development Kit
Utimaco Timestamp Server
Utimaco SecurityServer Se Gen2
Utimaco SecurityServer Se Gen2
*Secure key storage and processing
*Extensive key management
*Secure key storage inside HSM, as encrypted key blobs in file system or in enterprise-grade database
*2-factor authentication with smartcards “m out of n” authentication (e.g. 3 out of 5)
*Configurable role-based access control and separation of functions
*Multi-tenancy support
*Remote management
*Software simulator for evaluation and integration testing
*Supported operating systems: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
*All features included in product price
*Extensive key management
*Secure key storage inside HSM, as encrypted key blobs in file system or in enterprise-grade database
*2-factor authentication with smartcards “m out of n” authentication (e.g. 3 out of 5)
*Configurable role-based access control and separation of functions
*Multi-tenancy support
*Remote management
*Software simulator for evaluation and integration testing
*Supported operating systems: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
*All features included in product price

Key Features:
Capabilities
*Secure key storage and processing
*Cryptographic offloading/acceleration
*Extensive key management
*Key storage inside HSM or as encrypted key files
*Multiple options for user authentication and access control
*SmartCard for strong authentication
*“n out of m” authentication
*Separation of duties
*Remote Management
*Supported OS: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
*Cryptographic offloading/acceleration
*Extensive key management
*Key storage inside HSM or as encrypted key files
*Multiple options for user authentication and access control
*SmartCard for strong authentication
*“n out of m” authentication
*Separation of duties
*Remote Management
*Supported OS: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
Low operational costs
*Highest performance at an attractive price
*Inexpensive starter models for applications with lower performance requirements
*Extensive remote administration
*Efficient key management and firmware updates via remote access
*Automation of remote diagnosis through network management system using SNMP protocol
*Inexpensive starter models for applications with lower performance requirements
*Extensive remote administration
*Efficient key management and firmware updates via remote access
*Automation of remote diagnosis through network management system using SNMP protocol
Cryptography
*RSA
*ECDSA, NIST and Brainpool curves
*DSA
*DH, ECDH
*AES
*DES, Triple DES
*SHA-1, SHA-2, RIPEMD
*MAC, CMAC, HMAC
*Hash-based Deterministic Random Number Generator (DRNG)
*True Random Number Generator (TRNG)
*ECDSA, NIST and Brainpool curves
*DSA
*DH, ECDH
*AES
*DES, Triple DES
*SHA-1, SHA-2, RIPEMD
*MAC, CMAC, HMAC
*Hash-based Deterministic Random Number Generator (DRNG)
*True Random Number Generator (TRNG)
Application Programming Interfaces (APIs)
*PKCS#11
*Java Cryptography Extension (JCE)
*Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) and SQL Extensible Key Management (SQLEKM)
*Cryptographic eXtended services Interface (CXI)
*Utimaco‘s high performance interface guarantees easy integration of cryptographic functionality into client applications
*Java Cryptography Extension (JCE)
*Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) and SQL Extensible Key Management (SQLEKM)
*Cryptographic eXtended services Interface (CXI)
*Utimaco‘s high performance interface guarantees easy integration of cryptographic functionality into client applications
Security, safety, environmental compliance
*FIPS 140-2 Level 3
*CE, FCC Class B
*UL, IEC/EN 60950-1
*CB certificate
*RoHS II, WEEE
*CE, FCC Class B
*UL, IEC/EN 60950-1
*CB certificate
*RoHS II, WEEE
Technical Specification:
-Secure Communication
SecureDongle is built also with advanced encryption/decryption on communication between firmware and hardware to prevent debugging and emulator attacks.

SecurityServer SE Gen2 Brochure
Smarter way to protect your software!
Utimaco SecurityServer CSE
Utimaco SecurityServer CSE
Maximum security at highest performance
The SafeGuard® CryptoServer CSe-Series is a Hardware Security Module (HSM) which fulfills the highest physical security requirements. It contains special sensors which guarantee that all keys and certificates are actively deleted in the event of an attack. There are two available models for CSe-Series, in order to be able to satisfy diverse performance demands in different areas of application:
These allow the calculation of up to 100 and 500 RSA signatures per second respectively.
HSM Utimaco SafeGuard® CryptoServer CSe-series LAN
CS LAN’s more important function is as the central point of highest physical security for ePassport and eID applications. What makes it attractive is that it simplifies key management and its high availability features. It is aslo extremely scalable with no limitation regarding connections
HSM Utimaco SafeGuard® CryptoServer CSe-series PCIe
CS PCI also provides the Highest security HSM for eID and ePassport server applications. CS PCI is designed to optimize cryptographic acceleration in host applications. It has an integrated key management features and also delivers FIPS and Common Criteria compliance.
The SafeGuard® CryptoServer CSe-Series is a Hardware Security Module (HSM) which fulfills the highest physical security requirements. It contains special sensors which guarantee that all keys and certificates are actively deleted in the event of an attack. There are two available models for CSe-Series, in order to be able to satisfy diverse performance demands in different areas of application:
These allow the calculation of up to 100 and 500 RSA signatures per second respectively.
HSM Utimaco SafeGuard® CryptoServer CSe-series LAN
CS LAN’s more important function is as the central point of highest physical security for ePassport and eID applications. What makes it attractive is that it simplifies key management and its high availability features. It is aslo extremely scalable with no limitation regarding connections
HSM Utimaco SafeGuard® CryptoServer CSe-series PCIe
CS PCI also provides the Highest security HSM for eID and ePassport server applications. CS PCI is designed to optimize cryptographic acceleration in host applications. It has an integrated key management features and also delivers FIPS and Common Criteria compliance.

Key Features:
Maximum Security
*Highest performance at an attractive price
*Starter models for applications with lower performance requirements
*Extensive remote administration
*Efficient key management and firmware updates via remote access
*Automation of remote diagnosis through network management system using SNMP protocol
*Starter models for applications with lower performance requirements
*Extensive remote administration
*Efficient key management and firmware updates via remote access
*Automation of remote diagnosis through network management system using SNMP protocol
Capabilities
*Secure key storage and processing
*Cryptographic offloading/acceleration
*Extensive key management
*Key storage inside HSM or as encrypted key files
*Multiple options for user authentication and access control
*SmartCard for strong authentication
*“n out of m” authentication
*Separation of duties
*Remote Management
*Supported OS: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
*Cryptographic offloading/acceleration
*Extensive key management
*Key storage inside HSM or as encrypted key files
*Multiple options for user authentication and access control
*SmartCard for strong authentication
*“n out of m” authentication
*Separation of duties
*Remote Management
*Supported OS: Windows and Linux
*Multiple integrations with PKI applications, database encryption, etc.
Cryptography
*RSA
*ECDSA, NIST and Brainpool curves
*DSA
*DH, ECDH
*AES
*DES, Triple DES
*SHA-1, SHA-2, RIPEMD
*MAC, CMAC, HMAC
*Hash-based Deterministic Random Number Generator (DRNG)
*True Random Number Generator (TRNG)
*Security, safety, environmental compliance
*FIPS 140-2 Level 3, Physical Security Level 4**
*PCI HSM (w/ 3rd party firmware application)
*DK (German banking association)
*CE, FCC Class B
*UL, IEC/EN 60950-1
*CB certificate
*RoHS II, WEEE
*ECDSA, NIST and Brainpool curves
*DSA
*DH, ECDH
*AES
*DES, Triple DES
*SHA-1, SHA-2, RIPEMD
*MAC, CMAC, HMAC
*Hash-based Deterministic Random Number Generator (DRNG)
*True Random Number Generator (TRNG)
*Security, safety, environmental compliance
*FIPS 140-2 Level 3, Physical Security Level 4**
*PCI HSM (w/ 3rd party firmware application)
*DK (German banking association)
*CE, FCC Class B
*UL, IEC/EN 60950-1
*CB certificate
*RoHS II, WEEE
Application Programming Interfaces (APIs)
*PKCS#11
*Java Cryptography Extension (JCE)
*Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) and SQL Extensible Key Management (SQLEKM)
*Cryptographic eXtended services Interface (CXI)
*Utimaco‘s high performance interface guarantees easy integration of cryptographic functionality into client applications
*Java Cryptography Extension (JCE)
*Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) and SQL Extensible Key Management (SQLEKM)
*Cryptographic eXtended services Interface (CXI)
*Utimaco‘s high performance interface guarantees easy integration of cryptographic functionality into client applications
-HID Driverless
As HID driverless, SecureDongle requires no external device driver installation, thus minimizing the common technical issue arise from device driver. No driver is required. As long as a USB thumb drive is compatible with
-User-define security password
Supports on-board seed code and random number generation which developer can apply into their protection to strengthen the security and to make the protection more complicated to crack.
-Secure Communication
SecureDongle is built also with advanced encryption/decryption on communication between firmware and hardware to prevent debugging and emulator attacks.

SecureDongle Brochure
Smarter way to protect your sfotware!
Utimaco CryptoServer Software Development Kit
Utimaco CryptoServer Software Development Kit
SafeGuard® CryptoServer Se-Series is a Hardware Security Module (HSM) which is optimized for common security requirements in commercial environments. The SafeGuard® CryptoServer Se-Series is certified: FIPS 140-2 level 3. SE-Series offers the highest level of performance up to 12800 signatures per second.
The Se-Series provides investment security through open internal programming interfaces making it possible to integrate with almost any application in the secured area. The SafeGuard® CryptoServer Se-Series was developed for securing standard cryptographic operations in today’s security-critical business applications. Areas of application include identity management and PKI environments, document management and archiving solutions as well as database security.
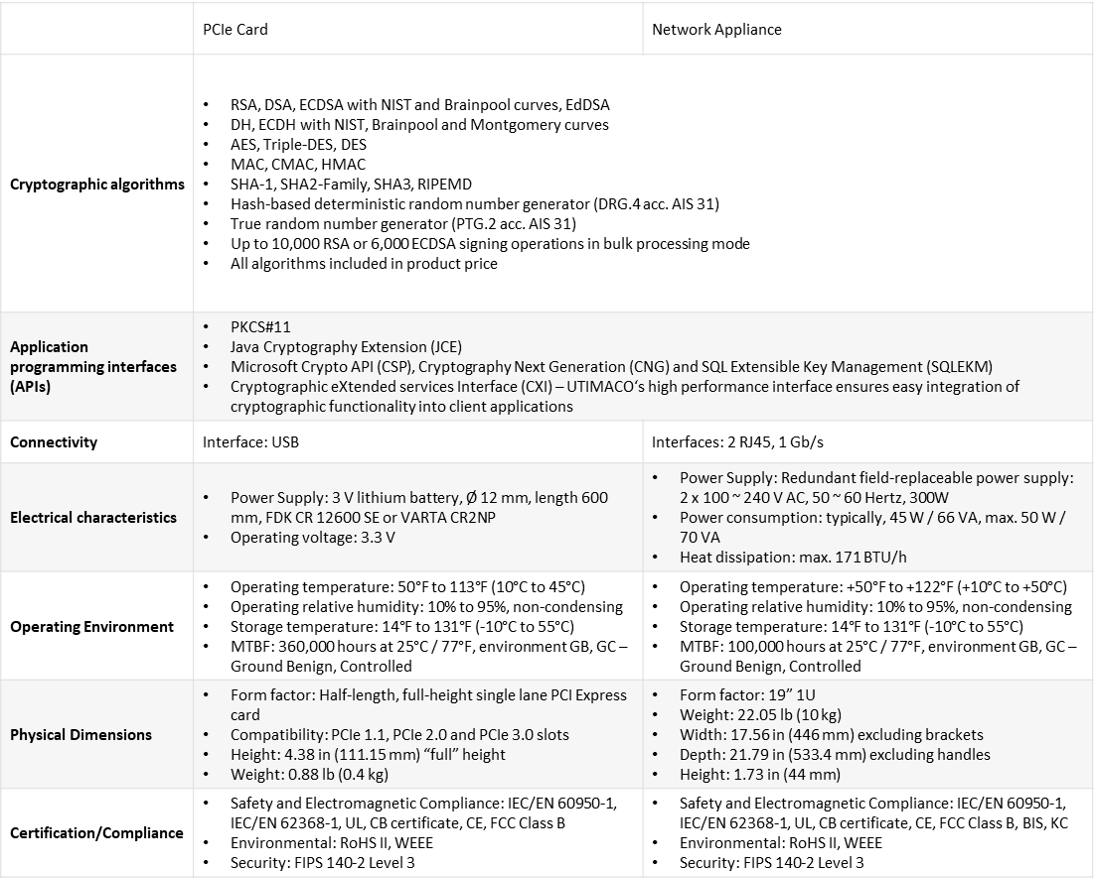
There are four models of Se-Series, in order to be able to satisfy diverse performance demands in different areas of application. These allow the calculation of up to 100, 500, 4000 and 12800 RSA signatures per second. All models are available as PCIe cards, which are suitable for all common PC and server architectures, and as 19″ network appliances, which are ideal for use in computer centers. Choose Se-Series if you need an industry standard HSM that is optimized for common security requirements in a commercial setting.
HSM Utimaco SafeGuard® CryptoServer Se-series LAN
As a Central point of security for critical applications, Se LAN simplifies encryption and signing of key management. Its high availability features ensures business continuity. It also offers extreme scalability with no limitation regarding connections
HSM Utimaco SafeGuard® CryptoServer Se-series PCIe
While Se PCIe offers a cost effective HSM for servers, it does not neglect performance as it is optimized for cryptographic acceleration in host applications. Se PCIe also has integrated key management feature.
The Se-Series provides investment security through open internal programming interfaces making it possible to integrate with almost any application in the secured area. The SafeGuard® CryptoServer Se-Series was developed for securing standard cryptographic operations in today’s security-critical business applications. Areas of application include identity management and PKI environments, document management and archiving solutions as well as database security.
There are four models of Se-Series, in order to be able to satisfy diverse performance demands in different areas of application. These allow the calculation of up to 100, 500, 4000 and 12800 RSA signatures per second. All models are available as PCIe cards, which are suitable for all common PC and server architectures, and as 19″ network appliances, which are ideal for use in computer centers. Choose Se-Series if you need an industry standard HSM that is optimized for common security requirements in a commercial setting.
HSM Utimaco SafeGuard® CryptoServer Se-series LAN
As a Central point of security for critical applications, Se LAN simplifies encryption and signing of key management. Its high availability features ensures business continuity. It also offers extreme scalability with no limitation regarding connections
HSM Utimaco SafeGuard® CryptoServer Se-series PCIe
While Se PCIe offers a cost effective HSM for servers, it does not neglect performance as it is optimized for cryptographic acceleration in host applications. Se PCIe also has integrated key management feature.

Key Features:
*Common Criteria EAL4+ certified
*Used in many WebTrust, CWA 14167 and eIDAS audited installations
*Integrity protected audit log (log signing), with digital signature or HMAC protection
*Full database integrity protection of all tables, to detect database manipulation
*Command line tool for verification of audit and database integrity protection
*Validation tool for conformance checking of certificates and OCSP responders
*EAC PKI (EAC 1.11 and 2.10) for ePassports and eIDs, Country Verifying CA (CVCA) and Document Verifiers (DV) issuing Inspection System (IS) certificates
*Certified access control and authorization module, for assurance and high trust role separation
*3GPP, i.e. LTE/4G, compatible PKI, using CMP with multiple Vendor CAs and vendor certificate authentication
*CMP Proxy to add an additional network layer, with message check, between the CA and CMP clients
*Command line CMP client in Java useful for scripting, testing and prototyping
*SCEP RA mode, using SCEP controlling entity creation from an RA
*SCEP Client Certificate Renewal, allowing client certificate renewal using SCEP
*Certificate Transparency, RFC6962
*CertSafe publisher to send, and revoke, certificates from a CertSafe server
*Peer Connectors for managing Peer Systems, such as OCSP Responders
*Direct Validation Authority (OCSP responder) updates from CA to VA. Ideal for low latency revocation and white listing
*External RA with a polling model for RA to CA communication, for high security environments. Ability to run the RA web UI in polling mode
*Create Crypto Tokens and CAs, generate keys and add and remove administrators through the Web Service API
*EV Certificate specific DN components as defined in CABForum guidelines (jurisdictionLocality, State and Country).
*eIDAS specific fields as defined in ETSI EN 319 412 (organizationIdentifier)
*Additional algorithms using HSMs through PKCS#11, RSASSA-PSS (SHA256WithRSAAndMGF1). Available through patches for Java
*Support for Native MS Autoenrollment in Windows environment with add-on autoenrollment proxy module
*Support for GOST and DSTU algorithms (Russian and Ukrainian algorithms)
*Penetration tested with improved security
*Used in many WebTrust, CWA 14167 and eIDAS audited installations
*Integrity protected audit log (log signing), with digital signature or HMAC protection
*Full database integrity protection of all tables, to detect database manipulation
*Command line tool for verification of audit and database integrity protection
*Validation tool for conformance checking of certificates and OCSP responders
*EAC PKI (EAC 1.11 and 2.10) for ePassports and eIDs, Country Verifying CA (CVCA) and Document Verifiers (DV) issuing Inspection System (IS) certificates
*Certified access control and authorization module, for assurance and high trust role separation
*3GPP, i.e. LTE/4G, compatible PKI, using CMP with multiple Vendor CAs and vendor certificate authentication
*CMP Proxy to add an additional network layer, with message check, between the CA and CMP clients
*Command line CMP client in Java useful for scripting, testing and prototyping
*SCEP RA mode, using SCEP controlling entity creation from an RA
*SCEP Client Certificate Renewal, allowing client certificate renewal using SCEP
*Certificate Transparency, RFC6962
*CertSafe publisher to send, and revoke, certificates from a CertSafe server
*Peer Connectors for managing Peer Systems, such as OCSP Responders
*Direct Validation Authority (OCSP responder) updates from CA to VA. Ideal for low latency revocation and white listing
*External RA with a polling model for RA to CA communication, for high security environments. Ability to run the RA web UI in polling mode
*Create Crypto Tokens and CAs, generate keys and add and remove administrators through the Web Service API
*EV Certificate specific DN components as defined in CABForum guidelines (jurisdictionLocality, State and Country).
*eIDAS specific fields as defined in ETSI EN 319 412 (organizationIdentifier)
*Additional algorithms using HSMs through PKCS#11, RSASSA-PSS (SHA256WithRSAAndMGF1). Available through patches for Java
*Support for Native MS Autoenrollment in Windows environment with add-on autoenrollment proxy module
*Support for GOST and DSTU algorithms (Russian and Ukrainian algorithms)
*Penetration tested with improved security
-Non-Smart Chip Based
Commonly based on a typical low cost EEPROM where the main protection algorithms rely more on the firmware that are bundle together rather than on the hardware. This type of hardware architecture can easily be duplicated by most Dongle Duplication Experts
-Self Definable Security Algorithms
Up to 128 self definable security algorithms that will be executed on-board when called by protected software which will then be authenticated using the popular Challenge Response Authentication to maximize the security level of the protection.
-Smart Chip Based
Advanced EAL4+ and ITSEC certified microprocessor smart chips enable the algorithm’s execution and on board seed code generation. Microprocessor smart chips also prevent hardware cloning and duplication attacks.
-Multi Levels Access Right Management
Supports multi level access right management to facilitate different access rights for the development team.
-HID Driverless
As HID driverless, SecureDongle requires no external device driver installation, thus minimizing the common technical issue arise from device driver. No driver is required. As long as a USB thumb drive is compatible with
-User-define security password
Supports on-board seed code and random number generation which developer can apply into their protection to strengthen the security and to make the protection more complicated to crack.
-Secure Communication
SecureDongle is built also with advanced encryption/decryption on communication between firmware and hardware to prevent debugging and emulator attacks.

SecureDongle Brochure
Smarter way to protect your sfotware!
Utimaco Timestamp Server
Utimaco Timestamp Server
TimestampServer is the ideal hardware security module for every business operation that requires the highest level of authenticity and tamper-proof creation of timestamps. We designed it to serve compliance requirements for applications with great legal or commercial significance.

User Benefits:
Especially suitable for business operations under highest commercial or legal requirements, Timestamp Server ensures your compliance standards are met.
Convenient fields of application:
*Document management systems
*Archiving solutions
*Electronic tender platforms
*Commercial Benefits
*Timestamp Server operates on all Utimaco network appliances and is available for unlimited connections without extra licenses.
*Archiving solutions
*Electronic tender platforms
*Commercial Benefits
*Timestamp Server operates on all Utimaco network appliances and is available for unlimited connections without extra licenses.
Secure investment:
*Highest performance at a cost-effective price point
*Open, modular software concept
*Long-term, easy upgrades to new procedures
*Interfaces
*A number of timestamp interfaces are included with Timestamp Server, which support Microsoft® Windows® and Linux operating systems.
*Open, modular software concept
*Long-term, easy upgrades to new procedures
*Interfaces
*A number of timestamp interfaces are included with Timestamp Server, which support Microsoft® Windows® and Linux operating systems.
Key interfaces:
*RFC 3161 timestamp protocol via HTTP or TCP, ETSI standard TS101861 compliant
*CryptoServer Timestamp API for general Timestamp Server administration and certification to PKCS#10 and PKCS#7
*Network Time Protocol with external time server syncing and support for Authenticated NTP
*Algorithms
*Timestamp Server leverages a host of popular timestamp algorithms, as well as additional algorithms upon request.
*CryptoServer Timestamp API for general Timestamp Server administration and certification to PKCS#10 and PKCS#7
*Network Time Protocol with external time server syncing and support for Authenticated NTP
*Algorithms
*Timestamp Server leverages a host of popular timestamp algorithms, as well as additional algorithms upon request.
Key algorithms:
*RSA
*Hash algorithms SHA-1, SHA-2 family, RIPEMD-160, MD5
*Hash algorithms SHA-1, SHA-2 family, RIPEMD-160, MD5
Technical Specification:
Builds of Choice
*Popular 19-inch network appliance allowing for a multitude of remote monitoring options
*Tamper Resistance
Tamper-resistant
*Active zeroization in case of temperature fluctuation or irregular energy supply, outside of defined limits
*Manual deletion possible
Technical Data
LAN appliance:
Power supply: 90~264 V, 47~63 Hertz AC, 2 x 420 W
Power consumption: typically 70 W / 85 VA, maximum 90 W / 100 VA
MTBF: 90,000 hours at 25° C / 77° F (in acc. with MIL-HDBK-217)
+10° C to +50° C (+50° F to +122° F)
Remote monitoring options
*Popular 19-inch network appliance allowing for a multitude of remote monitoring options
*Tamper Resistance
Tamper-resistant
*Active zeroization in case of temperature fluctuation or irregular energy supply, outside of defined limits
*Manual deletion possible
Technical Data
LAN appliance:
Power supply: 90~264 V, 47~63 Hertz AC, 2 x 420 W
Power consumption: typically 70 W / 85 VA, maximum 90 W / 100 VA
MTBF: 90,000 hours at 25° C / 77° F (in acc. with MIL-HDBK-217)
+10° C to +50° C (+50° F to +122° F)
Remote monitoring options
-HID Driverless
As HID driverless, SecureDongle requires no external device driver installation, thus minimizing the common technical issue arise from device driver. No driver is required. As long as a USB thumb drive is compatible with
-User-define security password
Supports on-board seed code and random number generation which developer can apply into their protection to strengthen the security and to make the protection more complicated to crack.
-Secure Communication
SecureDongle is built also with advanced encryption/decryption on communication between firmware and hardware to prevent debugging and emulator attacks.

SecureDongle Brochure
Smarter way to protect your sfotware!
1
%
of software installed on PCs around the world in 2015 were not properly licensed (a decrease from 43% in BSA’s previous global study published in 2014)
1
%
worldwide rate of unlicensed use in banking, insurance and securities industries (despite the fact that much tighter control of the digital environment is expected)
1
billion
The commercial value of unlicensed software worldwide plunged (BSA’s 2014 report cited commercial value of $62.7 billion)
Case Studies
National Cyber Security Agency (NACSA) & Securemetric Berhad
NACSA partners with Securemetric to enhance Malaysia's cybersecurity through FIDO2's passwordless authentication for critical information infrastructures.
Lazada Group’s Transition from EJBCA Community
Securemetric assisted Lazada Group's Transition from EJBCA Community to PKI-in-a-Box
Philippine Clearing House implemented PKI-In-A-Box to secure their clearing system
A significant stride was achieved when the Philippine Clearing House Corporation (PCHC) selected Securemetric to furnish and execute PKI-In-A-Box as a pivotal component of their nationwide digital security enhancement within their payment clearing system.
Universiti Utara Malaysia Entrusted Securemetric’s Microsoft Expertise
Since 2018, Securemetric's Microsoft Enterprise Solutions team, in collaboration with Sri Vision specialists, has been entrusted with the management of Universiti Utara Malaysia's IT infrastructure
Turnkey customized EJBCA Enterprise for Vietnam Government Information Security Commission
In the year 2015, Securemetric achieved a significant feat by securing a contract for a comprehensive turnkey PKI implementation for the Vietnamese Government, executed under the aegis of the Vietnam Government Information Security Commission (VGISC).…
Badan Siber Dan Sandi Negara upgraded to EJBCA Enterprise
Charged by the Indonesian government with the pivotal role of establishing and operating the Indonesia Government Certificate Authority, BSSN is entrusted with the issuance of digital identities and pivotal trust services to governmental entities nationwide.

SecureToken Brochure
SecureToken is an advanced secure microprocessor smart chip based USB token that integrates with powerful cryptographic technology designed for strong 2-Factor Authentication






