The new Android vulnerability discovered by Promon security researchers dubbed as StrandHogg is actively exploited by malwares to steal victims data. Both rooted and non-rooted devices running Android OS up to the latest Android 10 are impacted and vulnerable..
According to the security researchers, they found that all of the 500 most popular apps (as ranked by app intelligence company 42 Matters) are vulnerable to StrandHogg. Malwares such as Bankbot exploits this vulnerability to inject fake screens that overlays the authentic app screens to gain complete access and control over victim’s camera, SMS, phone call, GPS and other mobile resource.
On Android, activities from different apps are allowed to reside in the same task; such as opening a link from your email app, which will open the browser in the same task. When pressing the back button, the user will return back to their email application view.
“StrandHogg is unique because it enables sophisticated attacks without the need for a device privilege escalation (rooting), The vulnerability allows hackers to exploit a weakness in the multitasking system of Android to enact powerful attacks that allows malicious apps to masquerade as legitimate apps on the device,” says Promon.
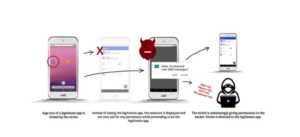
The vulnerability refers to the task Internal ID ‘taskAffinity’ of the target app and in doing so hijack the legitimate app tasks. In practice, this means that the user may click the target app icon in the launcher, but instead of seeing the target app’s activity, a malware activity overlays the legitimate app, thus hijacking the function of the legitimate app to gain almost complete control over the victims’ phone.
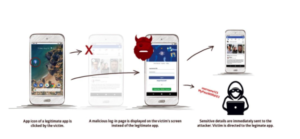
These malware activities are capable of requesting permissions by pretending to be legitimate permissions, Tricking victims into granting access of mobile phone functions to the malware.
Shielding Users and Mobile Apps from Unknown Vulnerabilities
How can we protect ourselves against serious Android vulnerabilities such as StrandHogg or other known and unknown vulnerabilities in the future.
Companies which facilitate their services via mobile apps should realize that, despite their developers ‘ efforts to protect their mobile apps, both Android OS and iOS can leave gaps that threaten their apps and users.

Securemetric offers SMobileShieldX (SMSX) a Runtime Application Self-Protection (RASP) solution that continuously monitors and prevents attacks at runtime on both Android and iOS mobile apps — detecting and shutting down potential malicious activity right away. One of the features of SMSX is to safeguard the mobile app from task-hijacking, which negates the StrandHogg vulnerability
Integrated directly to the mobile application, SMobileShieldX enables protection to be present in the application layer ensuring continuously real-time protection against static and dynamic attacks
For more details regarding the security features of SMobileShieldX, please contact our team here – sales@securemetric.com


